China’s hack of the Office of Personnel Management exposed the personal information of millions.
A computer nerd in North London, looking for military evidence of UFOs, shut down the Army’s Military District of Washington network of 2,000 computers for 24 hours.
And the hack — believed to be by Russian intelligence — of the Democratic Party’s emails roiled the 2016 election.
The Air Force doesn’t want to be next on that infamous list. And that spells opportunities for airmen who are interested in scoring bonuses and retention pay, retraining, and perhaps even a better shot at getting a promotion.
“There is a fight raging [in the cyber domain], make no doubt about it,” Maj. Gen. Patrick Higby, the Air Force’s director of cyberspace strategy and policy, told Air Force Times.
The Air Force has work to do. On Aug. 10, the service announced the results of the Hack the Air Force bug bounty program conducted earlier this year, in which it invited “white hat hackers” to ascertain where its weaknesses are, similar to the way a bank might hire a master thief to find soft spots in its vault.
The most successful hacker was a 17-year-old who submitted 30 valid reports of vulnerabilities. In all, more than 270 information security specialists from around the world discovered 207 cracks in the Air Force’s security and earned more than $130,000 in bounties.
The Air Force has roughly 22,000 active-duty cyber airmen, as well as another 10,500 National Guardsmen, 2,800 Air Force Reserve airmen and 9,700 civilians. Most are in the 24th Air Force, the service’s dedicated command responsible for operating, defending and sustaining the service’s cyberspace domain, but others are scattered through other organizations.
The Air Force isn’t looking for dramatic growth in the size of its cyber workforce, Higby said, but is rebalancing as it focuses its efforts on offensive and defensive cyber operations.
The majority of the 45,000 cyber airmen and civilians — about 36,000 of them — are assigned to run the Air Force’s network as part of the Department of Defense Information Network, or DODIN, operations. A smaller group of 837 are focused on defensive cyber operations, and another 286 conduct offensive cyber operations.
But now, the service is moving operations such as email, chat and voice to the cloud under the Collaboration Pathfinder project — freeing up DODIN ops airmen to move to offensive or defensive cyber operations.
When airmen make that move, Higby said, the biggest change will be adopting a different, “adversarial” mindset. They need to think like a hacker to figure out how someone might try to crack the Air Force’s systems, and sleuth out where the weaknesses might be.
“That causes you to say, ‘Oh, wait a minute, I need to pay attention to this setting,’ or ‘I need to make sure that these ports are actually closed,’ because that’s the way the adversary is going to come in to try to attack us,” Higby said.
Airmen moving to the offensive or defensive mission will also need to go through additional skills and mission qualification training, he said.
Those kinds of jobs, which carry a “coolness factor,” give cyber whizzes the chance to help defend their country — or to take on America’s enemies.

You can’t legally get that kind of offensive work in the private sector, he said.
“If you’re working for a bank or working on Wall Street or working for a large IT company, you can certainly defend yourself against cyberspace attacks, but you cannot, as we would say in the air domain, take the fight to the enemy,” Higby said.
Higby wouldn’t divulge what such hacking operations might entail, but said, “If you use your imagination, you can probably figure out what kind of things those airmen are doing at the behest of the United States Cyber Command commander.”
‘Troubling lack of focus’
The retention of cyber airmen is a serious problem, however.
During a May hearing, Sen. John McCain, R-Ariz., chairman of the Senate Armed Services Committee, sounded the alarm, noting that none of the 127 Air Force officers who recently finished their first tour in a cyber-related job stayed within the cyber field.
“That is unacceptable and suggests a troubling lack of focus,” McCain said. “It should be obvious that the development of a steady pipeline of talent, and retention of the ones we’ve trained already, is essential of the success of the cyber mission force.”
Higby said that when he’s asked if the Air Force has a cyber retention problem, he replies, “Yes and no.”
When it comes to 17D cyber officers, Higby said, the Air Force typically sees 70 percent to 75 percent come back for a second four-year stint after finishing their first four years. That’s more or less on par with other career fields across the Air Force, he said — but it’s not enough.
The Air Force also has historically under-assessed its cyber officers and has too many in higher, field grade officer positions — such as major, lieutenant colonel and colonel — and not enough company grade officers, such as lieutenants and captains. The problem was worsened by the force shaping cuts in 2007 and 2008, which led to a shortfall of company grade officers today, he said.
As a result, the Air Force now needs to hold on to about 90 percent of its officers — and it’s nowhere close to hitting that.
“We have to be a lot better,” Higby said. “We are not. We actually have more [field grade officer] authorizations than [company grade officer] authorizations. That means, if 100 percent of our captains stay in and get promoted to major, I’m still going to be short. Our pyramid is almost upside down.”
Bonuses and promotions
To try to fix its problems on both the officer and enlisted sides, the Air Force is upping its efforts to move airmen to the cyber world — and hold on to those already there.
For example, the Air Force in April began an officer retention bonus program for 17D cyber officers, allowing those with four to 12 years of service to extend their service in exchange for a $60,000 bonus.
In fiscal 2016, the Air Force added 1B4X1 cyber warfare operations to the list of career fields eligible for special duty pay, and then one year later upped their bonuses considerably, to $300 or $375 a month, depending on their skill level.
Earlier this year, the Air Force upped the selective re-enlistment bonus for cyber warfare operations airmen with between 17 months and six years of service, and expanded the bonus for those with 18 to 20 years of service. The bonus amounts for airmen with six to 14 years remained unchanged.
Retraining opportunities for NCOs to move into the 1B411 cyber warfare operations career field will increase in fiscal 2018. In 2017, there were 30 slots for staff sergeants and 35 slots for technical sergeants, but in 2018, that will rise to 44 for E-5s and 45 for E-6s. There are also slots for 80 first-term airmen to retrain into that career field in 2018 — the third-most of any AFSC, although that is down slightly from the 92 slots the previous year.
Although the Air Force in July slightly trimmed the list of career fields eligible for high year of tenure extensions — which give airmen more time to make rank before they are separated — it expanded eligibility for airmen in the cyber warfare operations career field.
Tech and master sergeants were already eligible, and now so are senior airmen and staff sergeants.
Some cyber career fields are also getting a considerable boost — particularly for E-5 through E-7 — when promotion time comes around. In most cases, career fields are promoted at the same rate across the service. But the Air Force has the power to up the selection rates of career fields that are undermanned in certain ranks.
For example, airmen in those ranks promoted in the 1B4X1 cyber warfare operations Air Force specialty code over the past year saw a selection rate that was anywhere from 8.75 to 10.5 percentage points higher than the Air Force average.
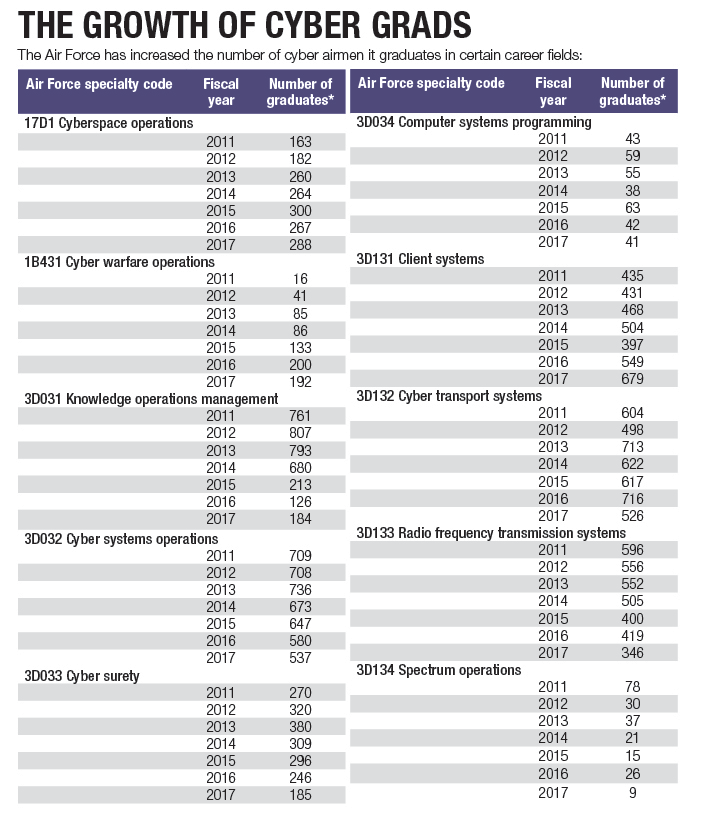
The Air Force is also increasing the number of 1B431 cyber warfare operations airmen it trains. In fiscal 2014, only 86 airmen in that field were trained, but by fiscal 2016, it had more than doubled to 200. And in the first 10 months of fiscal 2017, 192 had already been trained for that field.
The number of 17D1 network operations officers trained also increased from 264 in 2014 to 300 the next year. It dropped to 267 in 2016, but by the end of July, 288 had been trained in that field — almost matching the 2015 record.
And the Air Force Academy is guiding more new officers into the cyber world. Three years ago, only three academy graduates went on to join cyber career fields. By the time the class of 2017 graduated, that number increased to 27.
But trying to convince young cyber experts to put on Air Force blues for the first time isn’t easy.
In a May interview, then-Brig. Gen. Brian Kelly, the former director of military force management policy, said the improved job market — not to mention the growing demand for people with cybersecurity skills in the private sector and the rest of the military — has made it harder for the Air Force to recruit people with the same skill levels as it used to get.
“In the cyber area, … we’re getting the numbers we need and the basic quality we need,” said Kelly, who is now a major general and commander of the Air Force Personnel Center. “But as the competition has increased, we used to get even higher quality cyber folks, folks with what I would call additional credentials, exceeding our requirements. They came with previous cyber training and previous cyber certifications. … We continue to get some, but not as many as we would like. It’s getting to be a more challenging environment in the cyber world.”
Higby agreed and said one of the biggest recruitment and retention challenges facing the Air Force is that the United States isn’t producing enough cybersecurity experts.
“It’s a scarce resource,” Higby said. “So the challenge for the Air Force is, how can we entice a young man or young woman to join the cyber team, and be able to do some of these cool things to defend the nation?”

Air Force advantages
One big selling point for the Air Force, Higby said, is that it invests in training a lot more than many major commercial firms, which often expect new employees to already have certifications when they come on board. After the traditional seven weeks of basic training, apprentice cyber warfare operations airmen undergo 105 days of technical training, for example. New 17D cyberspace operations officers receive 115 days of training.
“You join the Air Force, we’re going to give you all the training you need,” Higby said. “They’re not going to be masters by the time they graduate [from technical training], but they’re going to have enough skills to be successful in learning new things at that first base we send them to. There are not a lot of other companies that invest that much time. … They’re going to expect you to already know, and already have all your certifications. They’re not going to help you do that.”
The Air Force also offers young airmen leadership opportunities within a few years. That — combined with the training and career experiences they’ll get — positions them to enter the private sector with an impressive portfolio when they decide to leave the service.
On the flip side, someone who has already studied cybersecurity and has commercial certifications such as A+, SEC+ or CISSP (certified information security systems professional) could come into the Air Force with an extra stripe, Higby said.
The fiscal 2017 National Defense Authorization Act authorizes the military to give newly commissioned reserve officers who have cyberspace-related experience or advanced education up to three years of constructive service credit. The Air Force, however, is still ironing out the finer points of how it will offer that credit, Higby said.
Down the road, the Air Force is looking at rolling out a new aptitude test to try to figure out which young people might have a knack for the cyber field.
It would be similar to the Defense Language Aptitude Battery test, Higby said, which doesn’t test whether someone knows a foreign language, but instead tests their potential for learning a new language.
The Air Force also could look in some unexpected places to find new airmen who could fill that role, he noted.
A young person who figured out how to get around security features and break into cars, for example, might not seem to be someone the Air Force wants on its cyber team, Higby said. But when he or she takes the cyber aptitude test, that expertise could demonstrate the “adversarial mindset” necessary for cyber operations.
“Then the question is, ‘OK, is this someone we can bring on the team, and then, through our Air Force training regimen, be able to instill the core values — excellence, integrity and service — into that young man or young woman?’ ” Higby said. “And then we bring those adversarial-minded skills onto the team to help us do our missions better.”
Stephen Losey is the air warfare reporter for Defense News. He previously covered leadership and personnel issues at Air Force Times, and the Pentagon, special operations and air warfare at Military.com. He has traveled to the Middle East to cover U.S. Air Force operations.